“Cybersecurity is not just about protecting computers, it’s about protecting lives,”. This quote is key to our talk about network security and ransomware. Ransomware locks your files and demands money to unlock them. A data breach can cost up to $4.35 million, showing the need for strong network security.
Creating a network security policy is vital. It outlines how to protect your network and who is responsible for security.
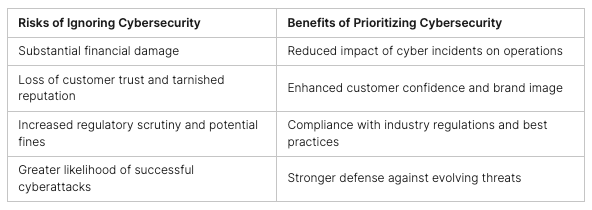
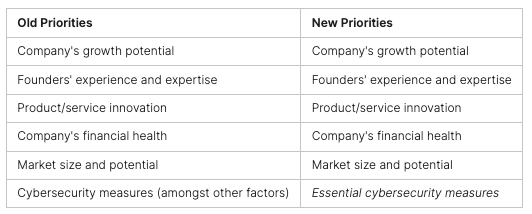
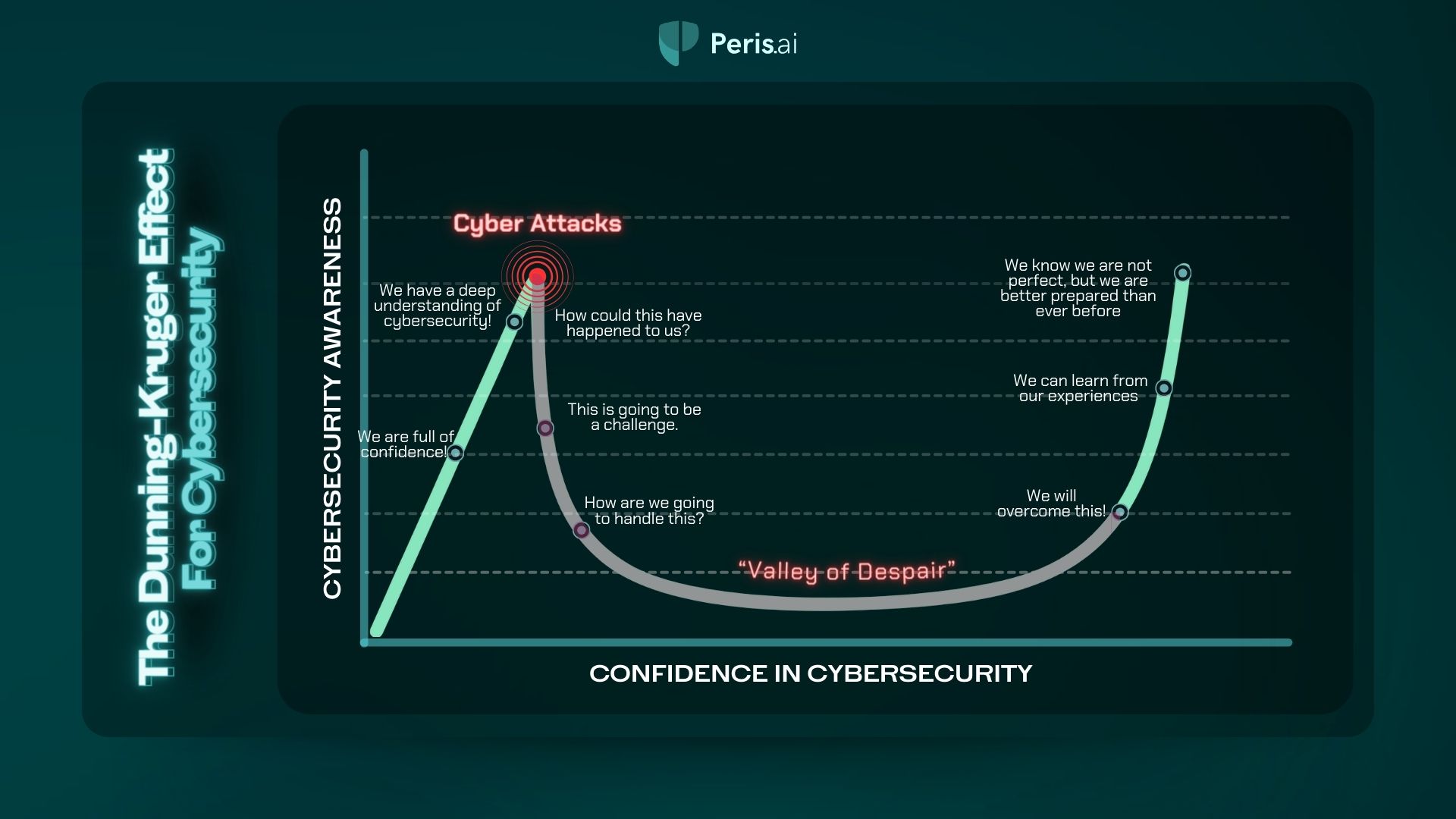
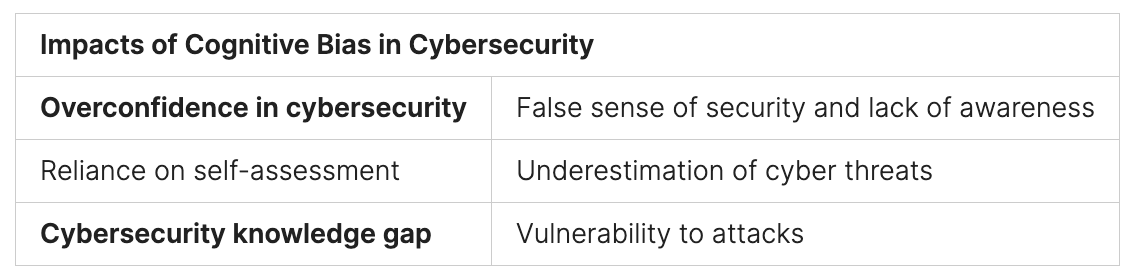
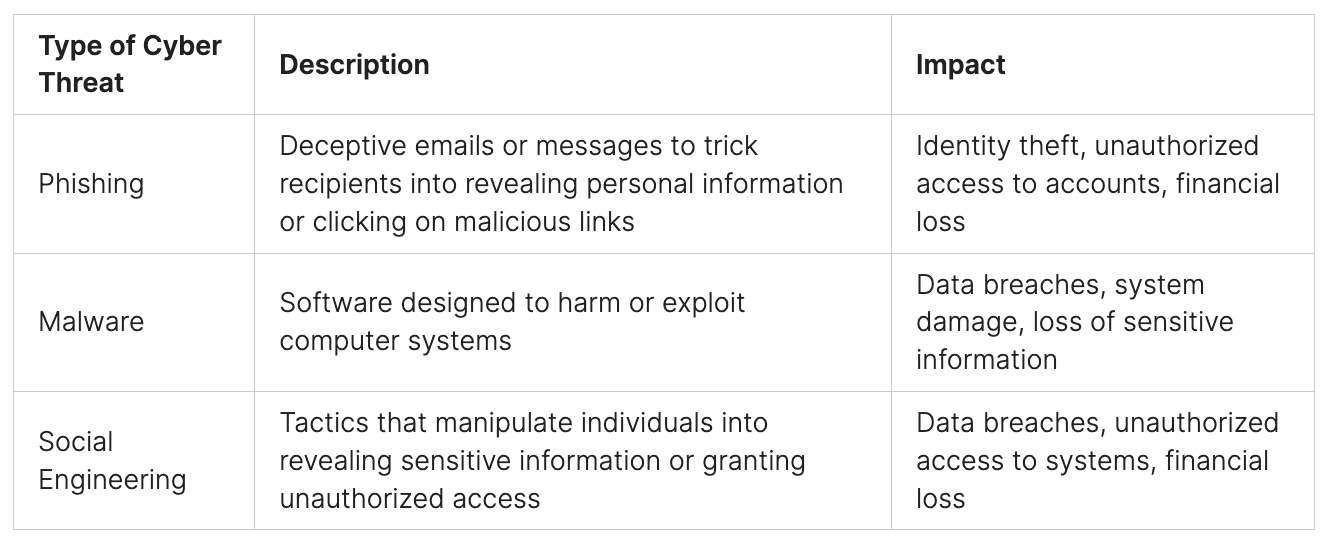
Stopping ransomware requires a complete approach. This includes understanding network security, preventing ransomware, and how network security stops it. Ransomware hits all kinds of places, from small towns to big companies.
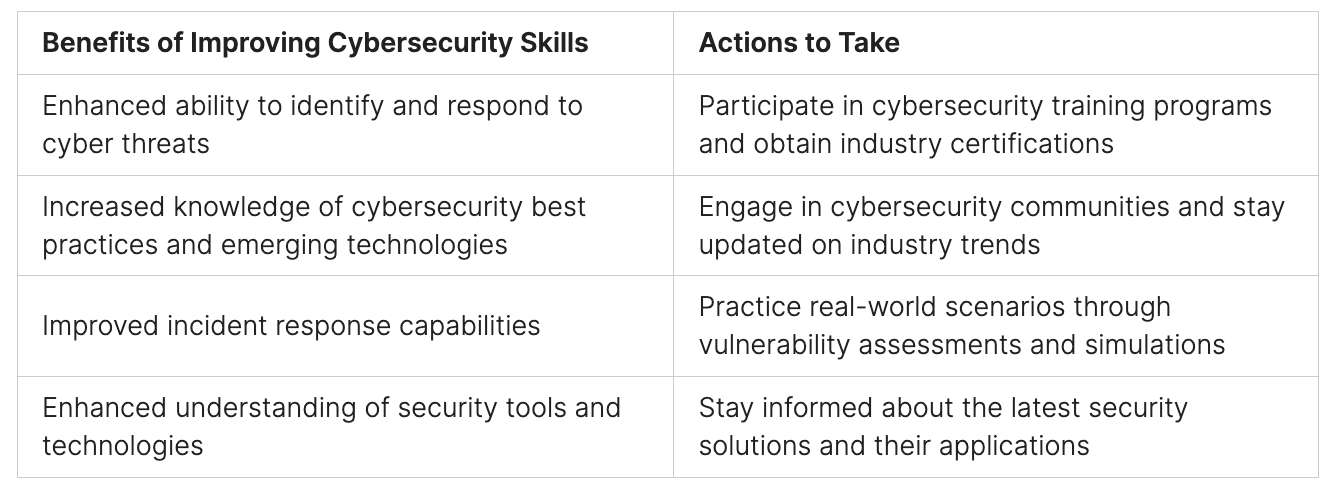
Training your team on network security is key. It makes them aware of security rules and helps them follow them. This reduces the chance of data loss.
Key Takeaways
- Network security is key in stopping ransomware and protecting businesses from big losses.
- Ransomware can shut down a business, causing lost productivity and revenue.
- Having a network security policy and training staff can prevent ransomware attacks.
- Backing up data is the best way to recover from ransomware.
- Keeping your systems and software up to date is critical to avoid security holes.
- Network security is vital in fighting ransomware, combining importance, prevention, and response.
- Network security is the first defense against ransomware attacks.
Understanding the Ransomware Threat Landscape
Ransomware attacks are a big threat to businesses of all sizes today. It’s key to know the current ransomware threats, including new trends and common ways attacks happen. Using strong cybersecurity tactics, like network security and ways to fight ransomware, helps protect companies.
Recent data shows healthcare was hit by 21% of ransomware attacks in 2023-2024, up from 18% the year before. This shows the importance of strong cybersecurity, even more so in healthcare. By using advanced tech, teaching employees, and having strict security rules, companies can lower their risk of ransomware attacks.
Some important ways to stop ransomware attacks include:
- Using strong and unique passwords
- Keeping software up to date
- Using antivirus and anti-malware software
- Teaching employees about security best practices
By focusing on these steps and keeping up with new ransomware threats, companies can improve their cybersecurity. This helps protect against these harmful attacks.
*Ransomware Reshaped: Evolving Your Defenses: https://youtube.com/watch?v=BW5kXQ3l61g
The Role of Network Security in Stopping Ransomware: A Comprehensive Overview
Stopping ransomware attacks needs a strong plan. This plan includes good cybersecurity and strong network security. Studies show that it takes 204 days to find a breach and 73 days to fix it. This shows we must act fast when ransomware hits.
We can do this by making good policies, keeping backups, knowing our weak spots, and making our network strong. Also, training our team is key.
Some important steps to stop ransomware include:
- Using a strong defense-in-depth approach for network security
- Doing regular security checks and tests
- Keeping all software and systems updated with the latest security fixes
Ransomware attacks have changed with the Ransomware-as-a-Service (RaaS) model. This has made attackers more skilled and work together. To fight back, we must keep up with the latest ransomware trends and threats.
By being proactive and covering all bases in network security, we can lower the risk of ransomware attacks. This means using strong cybersecurity, improving network security, and stopping ransomware attacks. We need technology, policies, and training our employees to stay safe.
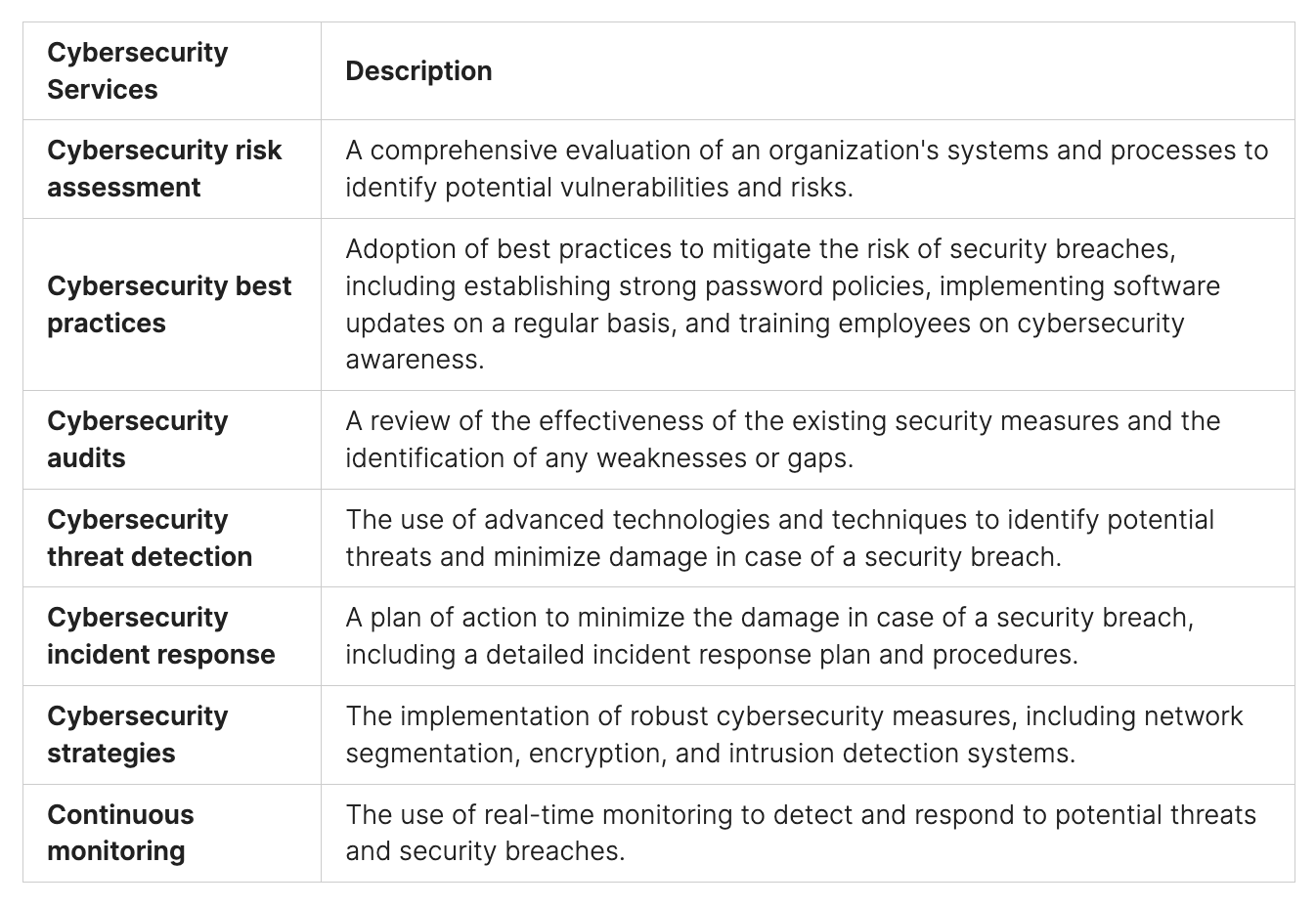
Essential Network Security Components for Ransomware Defense
It’s vital to have strong network security importance to stop ransomware attacks. Firewalls and intrusion prevention systems help block bad traffic. Also, using ransomware prevention strategies like network segmentation and access control is key. Keeping software and systems up to date is also important to fix security holes.
A solid plan for dealing with ransomware attacks is a must. This plan should cover prevention, detection, and recovery steps. It helps lessen damage and gets things back to normal faster. Teaching employees about security is also important to prevent attacks.
Some important cybersecurity defense tactics are:
- Using a layered security approach, or “defense in depth”
- Setting up strong security from the start
- Having a solid backup plan with regular backups and offsite storage
*a.Malware Attack Victim: The Evolution of a Cybersecurity Posture: https://youtube.com/watch?v=mV_5eG9q9LY
By using these strategies, companies can lower the chance of ransomware attacks. This makes sure their network security importance is strong.

Building a Robust Network Security Architecture
To stop ransomware attacks, it’s key to follow network security best practices. This includes using ransomware mitigation techniques and strategies to prevent attacks. By doing this, organizations can lower the chance of a successful attack. A strong network security architecture is vital in stopping ransomware. It offers a detailed plan to fight off different cyber threats.
Important parts of a strong network security architecture include using Zero Trust Network Access (ZTNA), next-generation firewalls, and advanced threat detection systems. Also, keeping up with security audits, updates, and employee access controls is important to prevent ransomware attacks. By sticking to these network security best practices, organizations can boost their security and lower the risk of a ransomware attack.
Also, using established frameworks and standards, like the NIST Cybersecurity Framework, helps organizations meet regulatory and industry standards. Combining these steps with ongoing employee training makes a strong defense against ransomware attacks. This protects sensitive data.
Creating a robust network security architecture needs a proactive approach. This includes regular assessments and audits to keep up with new cyber threats. By focusing on network security and following best practices, organizations can stop ransomware attacks and safeguard their assets.
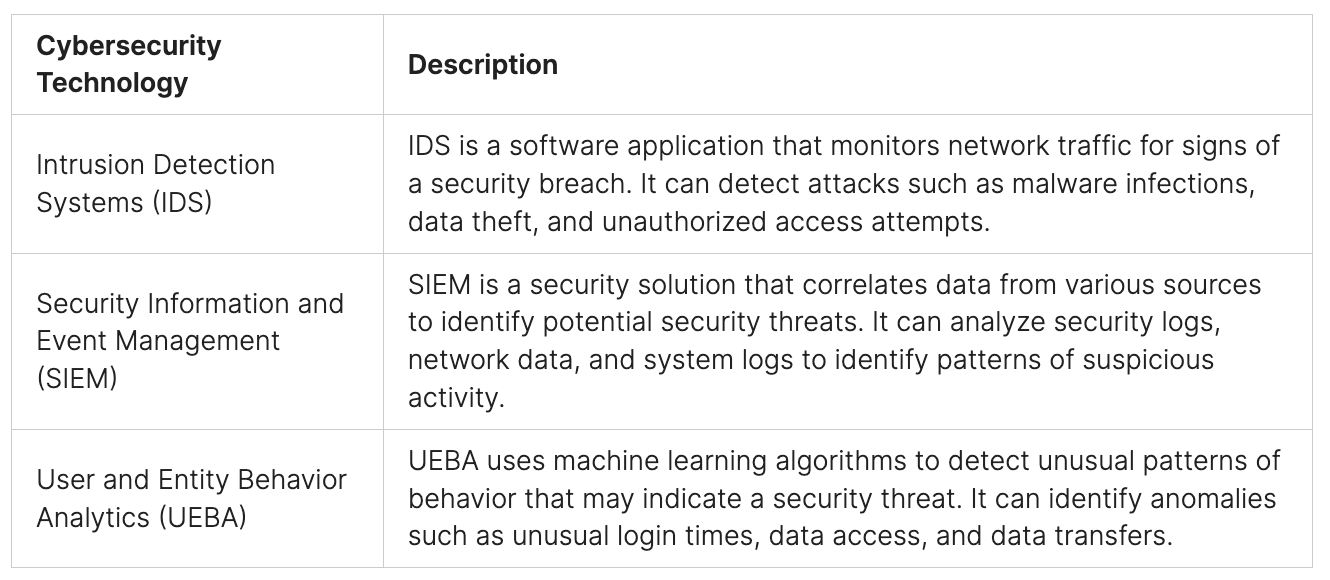
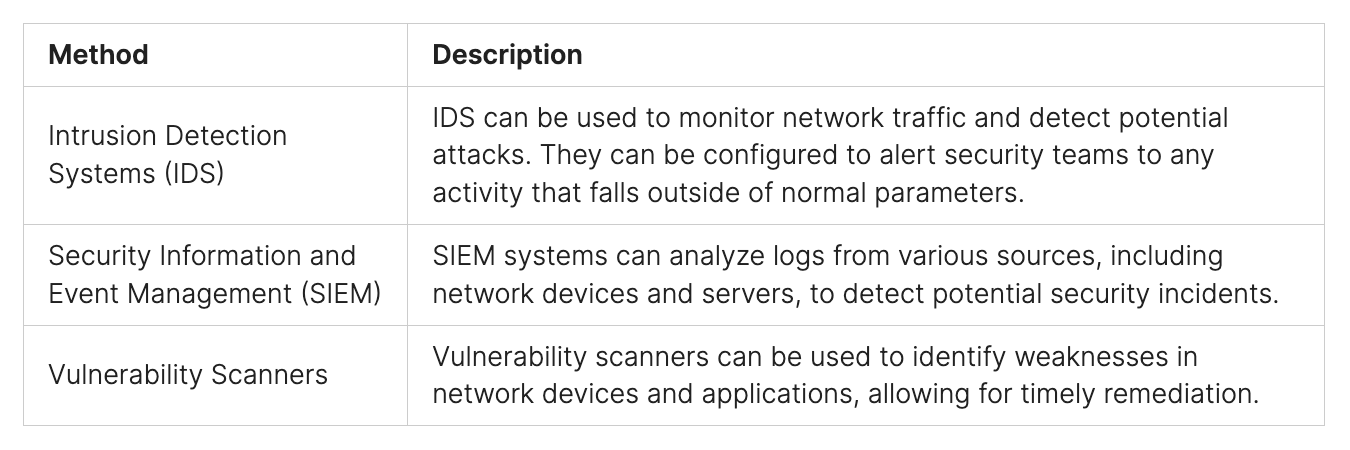
Implementing Advanced Threat Detection Systems
To protect against ransomware, it’s key to use advanced threat detection systems. These include real-time monitoring, behavioral analysis, and machine learning-based detection. These tools help organizations strengthen their cybersecurity, lowering the risk of ransomware attacks.
Preventing ransomware involves several steps. These include watching network activities, training employees, and using ATP tools. Also, keeping systems updated and backing up files can lessen damage from attacks.
To implement these steps, a mix of technology and best practices is needed. This includes:
- Real-time monitoring to quickly spot and act on threats
- Behavioral analysis to catch and stop odd activities
- Machine learning to keep up with new threats
By using these advanced systems and strategies, organizations can boost their network security. This helps protect against ransomware attacks.
It’s important to remember that these systems work best when they’re up to date. They must be regularly updated to fight off new threats.

Network Security Best Practices for Ransomware Prevention
To stop ransomware attacks, it’s key to follow network security best practices. This includes regular security checks, keeping software up to date, and controlling who can access the network. These steps help find and fix weaknesses that hackers might use. By focusing on network security, companies can lower the chance of ransomware attacks and lessen their damage.
Good ways to fight ransomware include using multi-factor authentication (MFA), dividing the network into parts, and setting up intrusion detection systems (IDS). These methods help spot and stop ransomware, and also slow down malware spread. Teaching employees about online dangers and how to stay safe is also important.
To make your network even safer, try these strategies:
- Use strong security to catch and stop ransomware attacks early
- Make sure antivirus software and other security tools are current
- Turn off ports in firewalls that you don’t need, like port 3389 for Remote Desktop Protocol
By sticking to these best practices and using good ransomware fight methods, companies can avoid ransomware attacks and keep their networks safe from cyber threats.
Incident Response and Recovery Strategies
Having a strong plan for dealing with ransomware attacks is key. It helps reduce damage and keeps your business running. First, you need to identify the type of malware and act fast to isolate affected systems to stop it from spreading. Recent data shows that industries like manufacturing and legal services are hit hard by ransomware.
A good plan includes cybersecurity defense tactics like regular checks and keeping software up to date. It also involves network security best practices like dividing your network and controlling who can access it. Plus, teaching employees about phishing and other scams is vital.
Important steps in handling a ransomware attack include:
- Isolating affected systems to prevent malware spread
- Identifying and patching vulnerabilities that allowed the breach
- Restoring data from backups and ensuring no infections in restored files
- Continuously monitoring systems post-recovery to identify any remaining vulnerabilities
These actions help organizations bounce back from ransomware attacks quickly. They reduce downtime and keep customers’ trust.
Integration of Security Tools and Protocols
Today, protecting networks from ransomware is more important than ever. Organizations can lower their risk by using strong cybersecurity measures. This includes using security tools and protocols to fight ransomware.
Recent data shows that 65% of financial organizations worldwide faced ransomware attacks in 2024. This is a big jump from 34% in 2021. This shows how critical it is to have good ransomware protection. Some important tools and protocols include:
- Security Information and Event Management (SIEM) systems, which help spot ransomware patterns.
- Zero Trust Architecture Implementation, which makes attacks less likely and less damaging.
- Cloud Security Integration, which uses access controls, encryption, and monitoring to keep cloud data safe.
Using these tools and protocols can make networks stronger against ransomware. This helps protect assets and keeps stakeholders’ trust.
*Cybersecurity in Healthcare: A Conversation with Trevor Dearing: https://youtube.com/watch?v=Z6G0FxZMAJ4
Future-Proofing Your Network Security
Digital technologies are more important than ever, making network security key. It’s vital to stop ransomware attacks to keep data safe and businesses running. Cybercrime damages are expected to hit $10.5 trillion by 2025, showing the urgent need for strong ransomware defense.
To keep your network safe, you must stay one step ahead of threats. This means using smart security systems and always improving. Important steps include:
- Using AI and machine learning to spot threats better
- Working together with other industries and governments to create strong cybersecurity plans
- Setting up a zero-trust system for network access, cutting down on unauthorized access by up to 30%
By focusing on network security and using strong ransomware defense, you can shield your business from ransomware harm. This ensures your business keeps running smoothly.

Conclusion: Strengthening Your Defense Against Ransomware
Ransomware attacks are a growing threat, costing businesses millions in damages. Protecting your organization requires a proactive cybersecurity strategy that combines advanced security measures, regular backups, and employee training. Implementing Zero Trust Network Access (ZTNA) and keeping software up to date are essential steps in reducing vulnerabilities.
Leveraging cutting-edge technologies like AI-driven threat detection can enhance security defenses, enabling businesses to detect and neutralize threats before they cause damage. A strong cybersecurity framework—built on network security best practices, employee awareness, and proactive risk management—is key to preventing ransomware attacks and securing sensitive data.
Stay ahead of cyber threats with Peris.ai. Visit Peris.ai to explore our cybersecurity solutions and safeguard your business from ransomware today.
FAQ
What is the role of network security in stopping ransomware attacks?
Network security is key in stopping ransomware attacks. It prevents unauthorized access and detects threats quickly. It also helps minimize damage to systems. By following best practices, like having policies and training, you can prevent these attacks.
What are the current ransomware attack trends and common attack vectors?
Today, ransomware attacks often start with phishing emails or exploited vulnerabilities. They also use unpatched software. Knowing these tactics helps organizations protect themselves better.
How can organizations enhance their network security for ransomware protection?
To protect against ransomware, use Zero Trust Network Access and firewalls. Network segmentation and access controls are also important. Regular updates and security audits help keep your network safe.
What are the essential network security components for ransomware defense?
Key components for ransomware defense include firewalls and intrusion prevention systems. Network segmentation and access controls are also vital. These tools help detect and prevent attacks, showing the importance of cybersecurity.
How can organizations build a robust network security architecture for ransomware protection?
A strong network security architecture starts with Zero Trust Network Access and segmentation. Access controls are also essential. This architecture boosts security and helps recover faster from attacks.
What are the benefits of implementing advanced threat detection systems for ransomware defense?
Advanced threat detection systems offer real-time monitoring and behavioral analysis. They use machine learning to detect threats. These systems are critical in preventing and responding to ransomware attacks.
What are the network security best practices for ransomware prevention?
To prevent ransomware, conduct regular security audits and keep software updated. Employee access controls are also important. These practices reduce the risk of attacks and protect systems.
How can organizations respond to and recover from ransomware attacks?
To respond to ransomware attacks, have an incident response plan ready. Identify the malware and minimize damage. Regular backups and disaster recovery plans speed up recovery.
What is the importance of integrating security tools and protocols for ransomware defense?
Integrating security tools like SIEM and Zero Trust Architecture is vital. Cloud security integration also plays a key role. These tools enhance security and help recover faster from attacks.
How can organizations future-proof their network security against ransomware attacks?
To stay ahead of ransomware, use emerging security technologies and adaptive architecture. Continuous improvement is also important. These steps help protect against evolving threats and improve overall security.