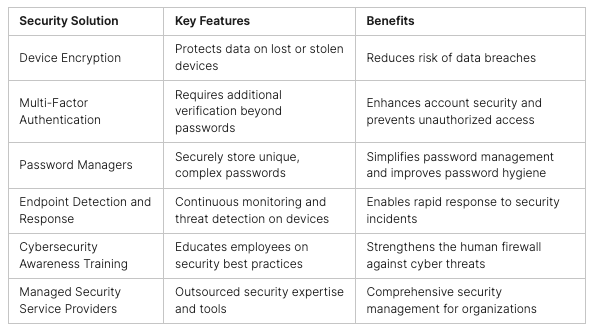
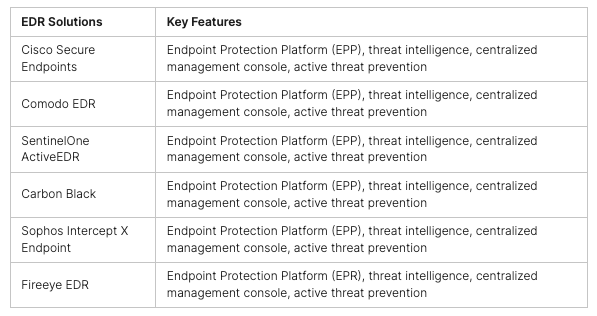
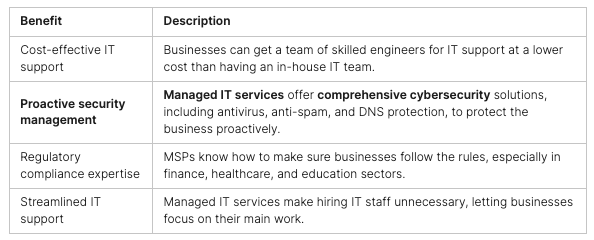
In today’s world, keeping our digital lives safe is more important than ever. We need to protect our personal messages and money transfers from prying eyes. Cryptography, a mix of math and computer science, is key to this digital safety.
This ancient art of hiding and revealing messages has grown with time. Now, it’s vital for keeping our online chats and transactions safe. But why is cryptography so important for our digital safety? And how does it adapt to new tech and threats?
Key Takeaways
- Cryptography is the foundation of digital security, safeguarding data confidentiality, integrity, and authentication.
- The field of cryptography has a long history, dating back to ancient civilizations, and has continued to evolve to meet modern challenges.
- Cryptographic algorithms, such as symmetric-key and asymmetric-key encryption, play a vital role in securing digital communications and transactions.
- Cryptographic protocols like SSL/TLS and digital signatures ensure the protection of sensitive information in everyday digital activities.
- Cryptography is essential in emerging technologies like blockchain and quantum computing, ensuring the continued security of our digital world.
The Importance of Cryptography in the Digital Age
In today’s world, data is key to our daily lives. The internet and computers have led to a huge increase in data. This has brought us closer together, sparking creativity and innovation. But, it has also made cybersecurity a big challenge. That’s why cryptography is vital for keeping our digital world safe.
The Pervasiveness of Data and the Need for Protection
Now, data is everywhere, making strong data protection and information security more important than ever. Cyber threats can harm individuals, businesses, and governments. This shows how crucial digital trust is in our digital lives.
Cryptography’s Role in Ensuring Confidentiality, Integrity, and Authentication
Cryptography is key to keeping our privacy and data safe. It encrypts data so only the right people can see it. This keeps it confidential. Cryptographic protocols also check the integrity of messages and prove who is sending them, ensuring authentication.
In short, cryptography is crucial for digital security. It protects our digital lives by keeping data safe and secure. As we use technology more, cryptography’s role in the digital age is more important than ever.
Cryptography Full Course | Cryptography And Network Security | Cryptography | Simplilearn: https://youtube.com/watch?v=C7vmouDOJYM
“Cryptography is the foundation of digital security, ensuring the confidentiality, integrity, and authentication of our data and communications in the digital age.”
The Fundamentals of Cryptography
Cryptography is the art and science of keeping data safe. It relies on two key parts: the algorithm and the key. The algorithm, or cipher, is a math function for encrypting and decrypting data. The key helps the cipher do these tasks.
Encryption and Decryption Algorithms
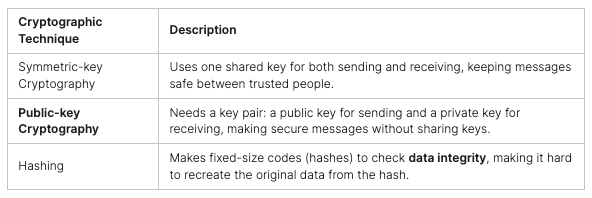
Cryptography has two main types: symmetric and asymmetric. Symmetric cryptography uses the same key for both encrypting and decrypting data. Asymmetric cryptography, or public-key cryptography, uses two different keys: one for encrypting and another for decrypting.
Symmetric and Asymmetric Cryptography
Symmetric-key cryptography is often used for keeping data secret because it’s fast and efficient. Asymmetric cryptography is used for key exchange, digital signatures, and verifying identity, since it doesn’t need a shared secret key.
Cryptographic algorithms, like DES and AES, help keep data safe, secure, and authentic. Hash functions, such as SHA-256 and MD5, turn data into fixed-size outputs to check data integrity and prevent tampering.

Cryptography is key for secure online transactions, digital signatures, password protection, and in military and intelligence fields. But, the rise of quantum computing could threaten current encryption methods. This means we need to keep improving cryptography to keep digital info safe.
Mathematical Foundations of Cryptography
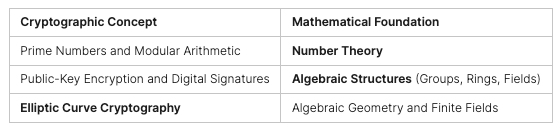
Cryptography is all about keeping messages safe. It’s built on number theory, a branch of math. Things like prime numbers and modular math are key to making secure systems.
Algebraic structures like groups and rings are also crucial. They help create secure ways to send messages and sign documents online. This math is essential for keeping our digital info safe.
Elliptic Curve Cryptography
Elliptic curve cryptography (ECC) is a special part of math used in crypto. It uses curves to make secure keys. ECC is strong like RSA but uses shorter keys, which is great for devices with less power.
The link between cryptographic mathematics and our digital safety is strong. As tech gets better, we’ll need stronger crypto solutions. So, math like number theory and algebra will keep being key to secure online talks.
Introduction to Cryptography: https://youtube.com/watch?v=-yfcTIKBPGw
“Cryptography is the essential building block of independence for organisations and individuals in the digital age.” – Eric Schmidt, former CEO of Google
Public-Key Cryptography: Secure Communication Without Prior Interaction
In today’s digital world, public-key cryptography is key for safe talks between people who’ve never met. It uses two keys: a public key shared openly and a private key kept secret.
RSA, a top public-key method, uses number theory for safe data sharing. To send a secure message, one uses the recipient’s public key for encryption. Only the private key can open it, keeping messages safe. This method means you don’t need to share keys before talking, changing the game for secure communication and key exchange.
Finding a private key by chance is like finding a grain of sand in the universe. Random Number Generation (RNG) uses computer processes and more to make private keys hard to guess or copy.
In Bitcoin and other digital coins, elliptic curve cryptography (ECC) makes public keys hard to turn back into private ones. Bitcoin uses SHA-256 and RIPEMD-160 to make a unique wallet address from the public key.
SSL certificates started using public key cryptography in the 1990s for online safety. Now, public key cryptography is key for keeping online data safe.
Companies need special ways to keep private keys safe, like cold storage wallets and multi-sig wallets. These keep important info safe and build trust with customers online.
“Public-key cryptography has changed how we safely talk online, letting unknown people share sensitive info with confidence.”

Cryptography in Everyday Life
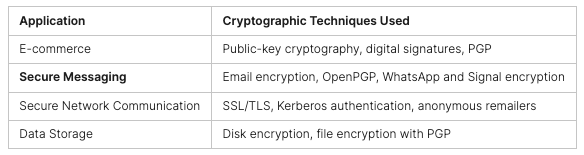
Cryptography is now a big part of our daily digital lives. It keeps our online activities safe. In e-commerce, it’s key for keeping our transactions secure. It protects things like credit card numbers and personal info. Apps like WhatsApp and Signal use end-to-end encryption to keep messages private, so only the intended people can read them.
E-Commerce and Online Transactions
E-commerce has made cryptography a must-have for secure online deals. Public-key cryptography is important for checking who sent a message and making sure it’s real. Tools like Pretty Good Privacy (PGP) add extra security to emails and files, making our digital chats safer.
Secure Communication and Messaging
Cryptographic methods are key to keeping our online chats and messages safe. Email encryption makes sure only the right people can read our messages. OpenPGP adds another layer of security to emails. Apps like WhatsApp and Signal use special codes to keep our messages safe and private.
“Cryptography is the foundation of digital security, ensuring the confidentiality, integrity, and authenticity of our online interactions and transactions.”
Cryptography is now a big part of our daily lives, keeping our data and messages safe. It helps with secure online shopping and private chats. Thanks to cryptography, we can trust and feel safe in our digital world.
Cryptography in Digital Security
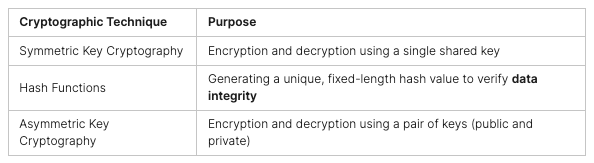
In today’s digital world, cryptography is key to keeping data safe. Data encryption helps protect sensitive info by making it unreadable to others. Digital authentication checks who you are, making sure you’re who you say you are, for safe online talks and deals.
Data Protection and Encryption
Data encryption is a big part of keeping data safe. It turns plain text into code that only the right people can read. This keeps your data private, stops others from getting in, and keeps it safe while it’s moving or being stored.
Authentication and Digital Signatures
Digital authentication is key to making sure you’re really who you say you are online. Digital signatures use special codes to prove you’re talking to the right people, keeping out fakes and fraud. This tech is used in many places, like online banking and government services.
Data Integrity and Hash Functions
Cryptographic hash functions help keep data safe by checking if it’s been changed. They make a special code from your data, so you can tell if it’s been messed with. This is super important in fields like healthcare and finance, where keeping data right is crucial.
Cryptography is used in many areas, from the military to entertainment. As we use more technology, the need for data integrity, digital authentication, and data encryption grows. It’s a key tool against cybercrime and protecting important info.

“Cryptography is not just about privacy and secrecy, but also about ensuring the integrity and authenticity of digital information.”
Cryptography helps in many fields, from the military to entertainment. As technology gets better, the role of data integrity, digital authentication, and data encryption grows. It’s vital in fighting cybercrime and protecting important info.
Challenges and Future of Cryptography
The digital world is always changing, and the ways we keep our online secrets safe are facing big challenges. Quantum computing, a new tech with huge power, is a big worry for old encryption methods. This new tech could break many encryption methods very fast and efficiently.
Also, cyber threats are getting worse, making it vital to have strong cryptographic resilience. Companies need to keep up with new threats and be ready for quantum computing’s impact.
Quantum Computing and Its Impact
By 2024, quantum computing will start to be a real threat in the cybersecurity world. Quantum computers can do lots of calculations at once, solving hard problems much faster than old computers.
Evolving Cyber Threats and the Need for Robust Cryptography
To fight these threats, experts are working on quantum-resistant cryptography, or PQC. Big groups like NIST, ENISA, and NCSC are leading the way, making sure we have strong encryption.
Switching to quantum-resistant cryptography is tricky because it must be secure, fast, and work with current systems. In 2024, we’ll see more global work on these new encryption methods because we need to get ready for quantum threats.
Waiting to use quantum-resistant cryptography could leave companies open to big risks. Moving to these new standards is hard because they might be slower and need bigger keys, but they’re key for keeping data safe.
In 2024, companies and cybersecurity experts should start moving to quantum-resistant standards to keep data safe. Keeping an eye on quantum computing and joining in on discussions is important for updating security plans.
Conclusion
Cryptography is key to keeping our digital world safe from threats. As cyber threats grow and new tech like quantum computing comes, we need strong cryptography more than ever. By focusing on cryptography, governments and companies can strengthen their defenses and keep people safe in our digital world.
It’s important to find the right mix of policy, money, and advanced cryptography for digital security. With more of our lives online, we need strong cryptography to protect us. Companies that use encryption, authentication, and data integrity will be ready for cyber threats and keep their customers’ trust.
In the end, cryptography leads the way in fighting fast-changing digital threats. By using cryptography and staying ahead of new challenges, we can make a safer digital future. This future will support innovation, protect privacy, and make us trust the digital world more.
FAQ
What is the role of cryptography in digital security?
Cryptography is key to keeping digital info safe. It uses complex math to protect information. This ensures that digital messages and transactions stay private and secure.
What are the two fundamental components of cryptography?
Cryptography relies on two main parts: the algorithm and the key. The algorithm is a math function for encrypting and decrypting data. The key is a special piece of data that helps with the process.
What are the two main types of cryptography?
There are two main types of cryptography. Symmetric cryptography uses the same key for both encrypting and decrypting data. Asymmetric cryptography, or public-key cryptography, uses two different keys: one for encrypting and another for decrypting.
What is the role of number theory and algebraic structures in cryptography?
Number theory is vital in modern cryptography. It deals with prime numbers and other math concepts crucial for many algorithms. Algebraic structures help build cryptographic protocols, like Elliptic Curve Cryptography (ECC).
How does public-key cryptography enable secure communication between parties?
Public-key cryptography lets people communicate safely, even if they’ve never met. It uses a public key that anyone can see and a private key that’s kept secret. RSA, a well-known algorithm, uses math to keep data safe.
How is cryptography used in everyday life?
Cryptography is used in many parts of our lives. It keeps online shopping safe and protects messages in apps like WhatsApp and Signal. This ensures our privacy and keeps our communications secure.
What are the key challenges facing cryptography?
Cryptography faces big challenges, like quantum computing, which could break some encryption methods. Cyber threats also keep getting worse, targeting weak spots in cryptography. This means we need to keep improving our encryption methods.