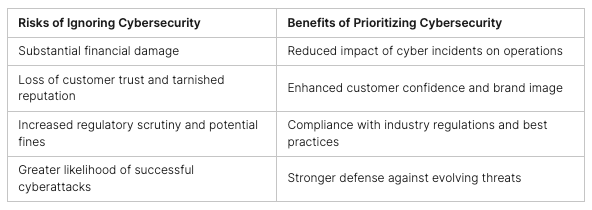
In the world of cybersecurity, being steps ahead of attackers is vital. Each year, thousands of new ways to attack systems are found. The time for hackers to use these flaws is getting shorter. So, how can we find and fix these problems before hackers strike? The answer is continuous penetration testing.
But, why do we need to keep testing constantly? Is this really the best way, making our systems deal with endless fake attacks? This article discusses why continuous penetration testing is a powerful way to protect your company. It’s all about staying safe from the changing threats out there.
Key Takeaways
- Continuous penetration testing is an ongoing adversarial attack simulation that closely emulates real-world threat actor tactics, techniques, and procedures (TTPs).
- Annual or semi-annual penetration tests can quickly become obsolete as new vulnerabilities are discovered, leaving organizations vulnerable to exploitation.
- Continuous testing provides a more cost-effective approach compared to traditional annual testing due to reduced ramp-up and reporting costs, as well as a better return on investment over time.
- Leveraging the MITRE ATT&CK framework and real-time vulnerability monitoring, continuous penetration testing offers superior insights and a stronger overall cybersecurity posture.
- By combining automated and manual testing methods, organizations can achieve comprehensive security coverage and effectively respond to emerging threats.
Understanding Penetration Testing
Penetration testing is also called a pen test or ethical hacking. It’s a way to test how strong a system’s security is. By simulating cyberattacks, you can see where the system is strong or weak.
What is Penetration Testing?
Penetration testing is a key step for all organizations. It helps see if their security policies really work. Then, they can make these policies better to avoid cyber threats.
Why Penetration Testing is Crucial
It’s critical for all organizations to do penetration testing regularly. This helps check the effectiveness of their security policies. And, it allows them to improve these policies to stop future cyber threats.
Annual Penetration Testing: An Ineffective Approach
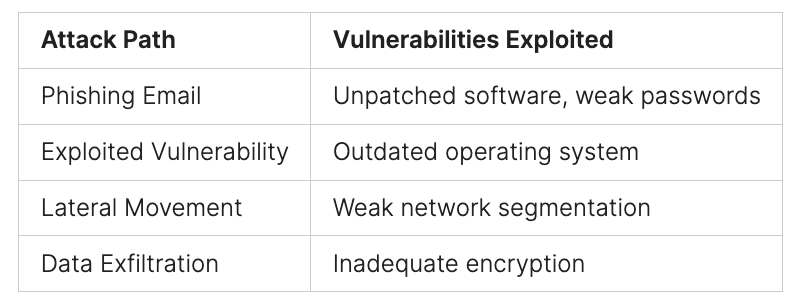
The problem with doing penetration tests once or twice a year is clear. New vulnerabilities are found all the time. In 2000, there were 1,438 security flaws known. But by 2023, this number grew to 21,085. Skilled attackers keep track of what technology a company uses. They do this to find ways to break in.
Vulnerabilities Are Constantly Emerging
Things get risky for businesses that test their systems just once a year. That’s because new cyber threats appear all the time. This makes it hard for companies to fix their security holes before attackers exploit them.
Attackers Exploit New Vulnerabilities Quickly
When a new security flaw is found, attackers move fast. They use the time before it’s fixed to their advantage. This game underlines why yearly security checks aren’t enough. Companies need to be always alert about their security.
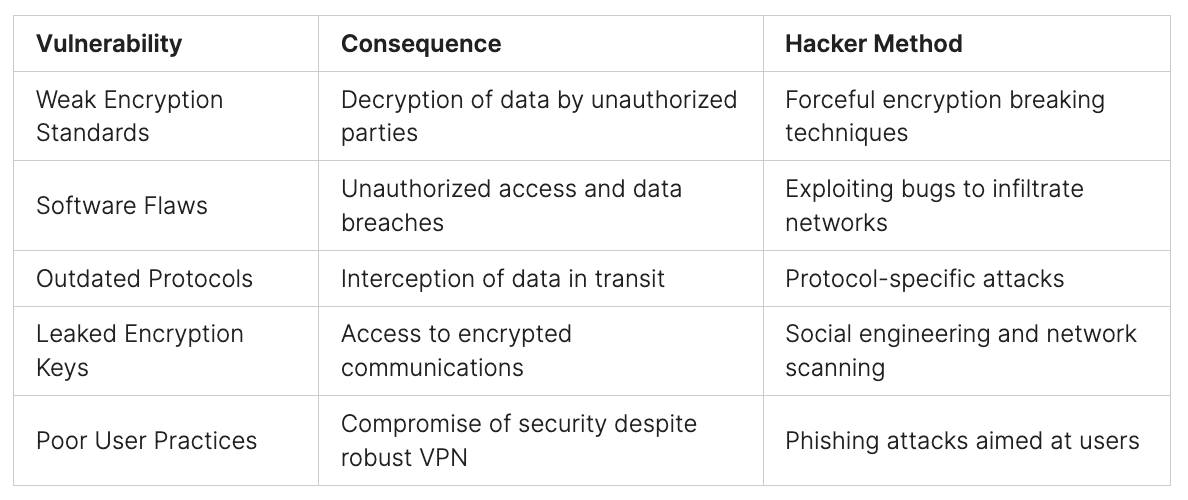
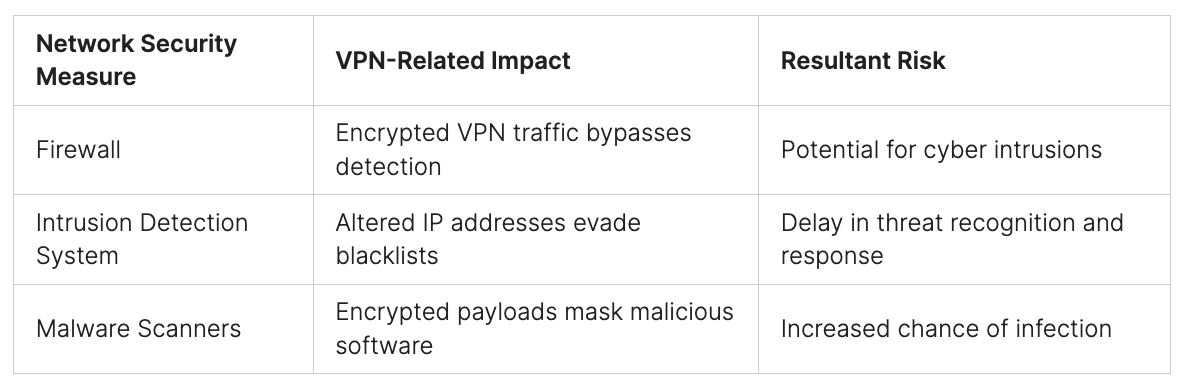
Limitations of Automated Scanning and IDS
Tools like automated vulnerability scanners and intrusion detection systems (IDSs) help keep organizations safe. But, they’re not enough alone. This is because they rely on signatures to spot possible dangers. This means they can miss new threats that don’t have known digital ‘fingerprints’ yet. So, it can be hard to stop these threats as they happen.
Signature-Based Detection Misses New Threats
The way automated scanners and IDSs work can’t always keep up with fast changes in cyber threats. If they don’t have the latest signatures, they might not find new problems. This leaves companies at risk of attacks or losing important data.
Case Study: Data Breach Due to Unpatched Vulnerability
For example, a big data breach recently happened. It exposed Personal Health Information (PHI) of about 4.5 million customers. Even with strong security efforts, the company couldn’t stop the attack. The problem was an old issue that their security didn’t catch and fix in time.
Continuous Penetration Testing
Continuous penetration testing is not like the usual one-time tests. It’s an always-on simulation of real-world attacks. By mimicking how real hackers act, it keeps organizations safe from new threats.
Baseline Assessment and Roadmap to Remediation
It starts with a Baseline Assessment to find weaknesses in system security. This step maps out a plan for fixing those issues. It gives a snapshot of how secure an organization is right now.
Threat Modeling and Attack Trees
The next step is Threat Modeling. Here, every software used is checked, and attack trees are made. These trees show how a weak software spot could harm the network. This helps focus on the most dangerous risks.
Directed Attacks Simulate Adversarial Behavior
Then comes the Directed Attacks phase. It imitates real attacks, aiming from different angles. This part is a mix of keeping up with the latest threats and testing the network against them, catching problems before hackers do.
This method uses MITRE ATT&CK and in-depth knowledge of hacker techniques. It offers a more precise view of security, allowing steps to be taken to fix any issues. Essentially, it makes the whole network defense stronger.
Cost-Effectiveness of Continuous Penetration Testing
Many companies worry that continuous penetration testing costs too much. Yet, it can actually be cheaper over time than annual or semi-annual tests, especially when done by an outside team. Several reasons make this possible.
Reduced Ramp-Up and Reporting Costs
Continuous testing keeps an eye on an organization’s IT changes. It looks closely at specific infrastructure changes, not everything. This saves money on getting ready and writing reports, which can cost thousands each year. In traditional tests, a lot of time and money go into these extra tasks.
Focused Testing on Infrastructure Changes
With continuous testing, the team looks at new IT changes from the last check-up. This focused testing approach saves more money than the general tests done annually or semi-annually.
Return on Investment over Time
After the first year, the benefits of continuous security testing are clear. It saves a lot of money over time. This is because it reduces the need for big start-up and report-writing costs.
Continuous Penetration Testing
Continuous penetration testing learns from today’s threat actors tactics and techniques. It simulates attacks to test defenses. This includes trying to get initial access, assuming a breach, and what happens after.
Emulating Real-World Threat Actor TTPs
By acting like real threat actors, continuous testing tells how secure a system really is. It makes security teams smarter by showing real attack methods. This way, they can make better defenses.
Leveraging MITRE ATT&CK Framework
The MITRE ATT&CK framework is great for making attack simulations. It helps make tests that look like real threats. It gives a common way to talk about attacks, helping teams stay on top of the latest threats.
Real-Time Vulnerability Monitoring
Testing also keeps an eye on new security alerts. It checks which could be trouble for the company. This keeps the system safer by fixing issues before they’re used against the company.
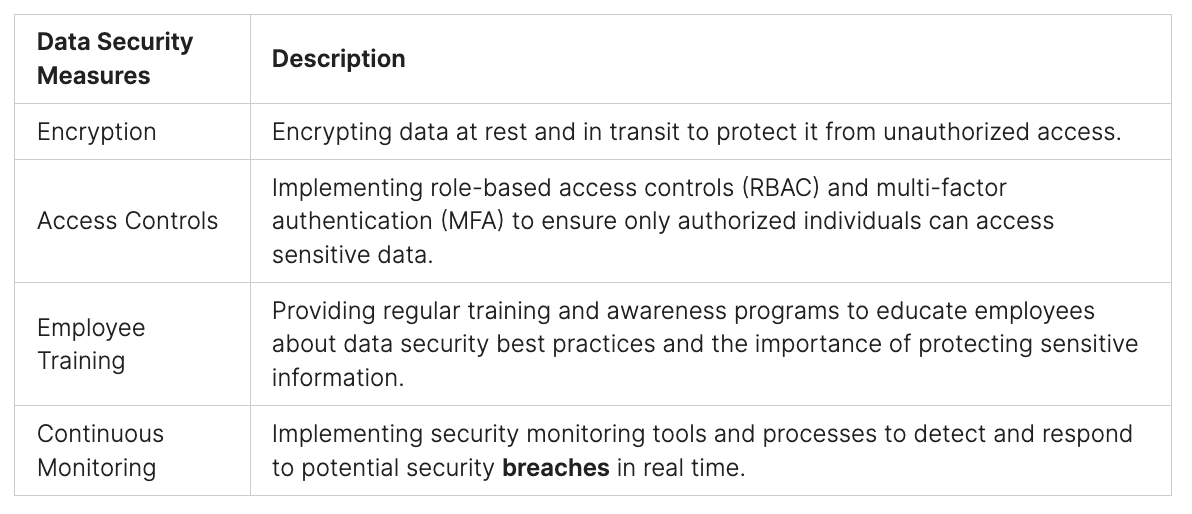
Combining Automated and Manual Testing
Great security checks need both automatic tools and human insights. Tools like scanners and monitors see threats in real time and alert us to problems. They check for weaknesses all the time.
Automated Tools for Efficiency
Automatic tools find known problems quickly across big networks. They make detailed reports fast, helping companies keep up with dangers. Yet, they might not catch complex issues that need human review.
Manual Processes for In-Depth Analysis
But, humans are still needed for a deep look. Security experts check the machine results, figure out the best fixes, and make sure important issues get fixed first. They dig through the security to understand its real strength.
Combining tools and human checks makes security strong. It means finding and fixing problems before they get critical. This mix ensures a company’s defenses stay sharp.
Establishing a Clear Testing Flow
A proper penetration testing flow is vital for finding and dealing with security threats in real time. It involves many stages working together. These include finding, looking at, and fixing weak spots in a company’s setup.
Enumeration and Vulnerability Assessment
The Enumeration stage is first. It collects info like active systems and open ports. Then, the Vulnerability Assessment phase takes a closer look. It finds the exact weak spots that hackers might use.
Exploitation and Post-Exploitation
The Exploitation step tests these weak spots with real attacks. This helps understand how bad they could be if used by hackers. If an attack works, the Post-Exploitation phase follows. It allows going deeper into the system and checking how far a hacker could get.
Lateral Movement and Proof of Concept
Lateral Movement and Proof of Concept are the last steps. Lateral Movement mimics how a real attack could spread through a network. Proof of Concept makes detailed reports about what was found. This helps the company know exactly what to fix.
Having a clear testing flow helps testers stay in control. They can make sure every detail about the business is considered. This is important for checking how secure the company really is.
Determining Testing Frequency
Organizations must decide how often to run penetration tests. They should think about the worst things that could happen. Then, they should match the test schedule with their work on new products or updates.
Doing yearly tests is the minimum. But, it’s better to test often to keep up. For example, continuous penetration testing helps spot risks quickly. This is important because risks are always changing.
Aligning with Development Cycles
It’s crucial to test often, following when new software is made. This way, any new risks that updates bring get caught fast. This becomes even more critical as companies add new features or change their software or network.
Considering Worst-Case Scenarios
Thinking about the worst that could happen guides how often to test. This method ensures better protection against major risks. It helps focus testing on the most important parts regularly.
Implementing Continuous Penetration Testing
Penetration testing is a detailed check on security for apps, networks, and tech systems. When companies do continuous penetration testing, they get thorough reports. These reports include the found vulnerabilities, what they are, how to attack, and what happens if they succeed.
Detailed Vulnerability Reports
Full vulnerability reports tell companies the state of their tech security. They show the problems found, how a hacker could use them, and what they could do. Knowing these issues helps organizations to smartly fix them, making their tech safer.
Impact Assessment and Recommendations
The continuous penetration testing should say what could happen if a hacker wins. This helps focus on fixing the most dangerous issues first. The reports also give step-by-step recommendations on how to make things better. This way, companies can build a stronger cybersecurity defense
Conclusion
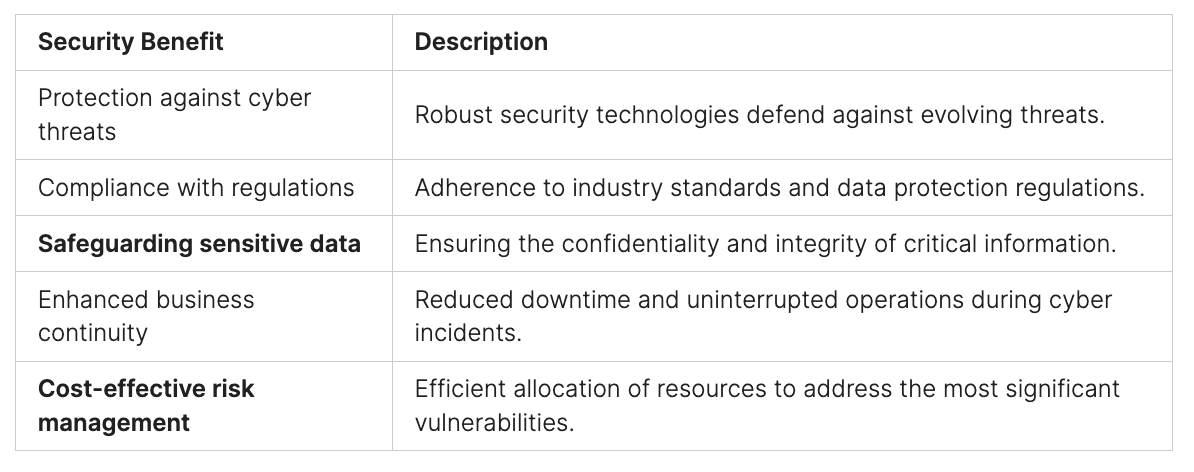
With over 2,000 new information security issues emerging each month and skilled cyber attackers constantly at work, the necessity for continuous penetration testing has never been more critical. Annual penetration tests quickly become outdated, leaving systems vulnerable shortly after assessments are completed. By engaging in continuous penetration testing, organizations can stay ahead of current cyber threats and maintain stronger defenses.
This proactive approach allows companies to identify and address vulnerabilities before they escalate into significant problems, effectively preventing costly cyber attacks and ensuring a high level of protection. As cyber threats become increasingly sophisticated, continuous penetration testing provides invaluable insights and strengthens overall security measures, helping organizations to stay resilient against persistent cyber adversaries.
Ensure your business remains secure and gains a competitive edge with Peris.ai Pandava. Sleep better knowing your data is safe with our thorough penetration testing and detailed reports. Our ethical hackers will identify vulnerabilities and weak points within your digital platforms and infrastructures, allowing you to address them before they are exploited.
Don’t wait—visit Peris.ai Cybersecurity to learn more about Peris.ai Pandava and how our services can help you safeguard your business against evolving cyber threats. Secure your digital future today!
FAQ
What is penetration testing?
Penetration testing, or pen test, is like ethical hacking. It checks how secure a computer system is. This kind of testing looks for ways attackers could get in and what’s already strong.
Why is penetration testing crucial?
It’s key for any group to do pen tests regularly. They show if security rules actually work. Then, those rules can be made better to stop cyber threats.
What are the limitations of annual penetration testing?
Doing pen tests once a year or so has downsides. New vulnerabilities are found fast. Attackers can use this time to plan their moves before areas are secured.
Why are automated scanning and IDS not enough?
While good for everyday checks, they can miss new threats. This is since they look for specific signs, not keeping up with all the latest dangers.
What are the key components of continuous penetration testing?
It’s like always preparing for the worst. This means mimicking what real attackers could do often. It starts with setting a standard. Then, the tests get more direct and real as time goes on.
How is continuous penetration testing more cost-effective?
By always watching and reacting quickly, it’s cheaper in the long run. Doing power-up checks all the time becomes unnecessary. Plus, it saves a lot of time in figuring out the reports.
How does continuous penetration testing emulate real-world threat actors?
It learns from attackers’ latest moves and adapts fast. This means it tests from all points of possible attack, just like real threats. It also keeps up with the most current dangers.
What is the importance of combining automated and manual testing?
Both types are needed for security. Automating finds threats quickly, but manual checks give a deep look. They’re crucial in understanding the findings and planning for safety.
What is a well-defined testing flow for penetration testing?
The steps include learning about the system, checking for weak spots, trying to get in, deepening access, moving through the network, and proving attacks can really happen. This method leaves no stone unturned.
How should organizations determine the frequency of penetration testing?
They need to be alert and test as new risks come up. Yearly checks are just a start. But, keeping up with attacks and fixes is the smart play.
What are the key benefits of implementing continuous penetration testing?
It helps spot and fix problems before real damage. You’ll get info on threats and how they could hurt, plus ways to stay ahead of attackers. This keeps your defenses strong all the time.