Capture the Flag (CTF) competitions are becoming a big deal in the fast-changing world of cybersecurity. They’re not just for tech experts; they show us what modern cybersecurity pros are like. But what do these competitions teach us? You might be surprised.
CTF competitions are more than a hobby for cybersecurity fans. They mirror the real challenges faced by professionals every day. These events are big in the cybersecurity world and happen at conferences and gatherings, showing a lot of interest and participation. They let people practice finding vulnerabilities, reverse-engineering software, and solving tough problems in a safe, legal way. It’s a chance for individuals to improve their skills and compete with the best out there.
Key Takeaways
- Capture the Flag competitions offer a unique hands-on approach to cybersecurity training and skill development.
- These competitions simulate real-world security challenges, preparing participants for the realities of the industry.
- Participation in CTFs can lead to valuable networking opportunities and career advancement.
- CTFs foster a culture of innovation, problem-solving, and collaborative thinking in cybersecurity.
- Organizing and running CTF events presents its own set of challenges, but the benefits for the community are undeniable.
As we explore Capture the Flag further, we’ll see the valuable lessons these competitions offer. They teach us about ethical hacking, teamwork, and strategic thinking. These insights are set to change how we handle digital security in the future.
Introduction to Capture the Flag (CTF) Competitions
CTF competitions are thrilling events where players, alone or in teams, aim to find and use system weaknesses to get a “flag” or secret info. They come in two main types: Jeopardy-style and Attack-Defense.
What are CTF Competitions?
In Jeopardy-style CTFs, players solve questions to get clues and earn points. Attack-Defense CTFs have teams defend their PCs while attacking others, earning points for finding flaws.
Types of CTF Competitions
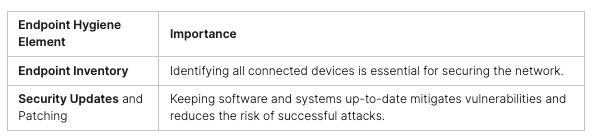
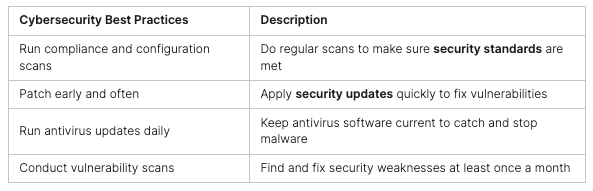
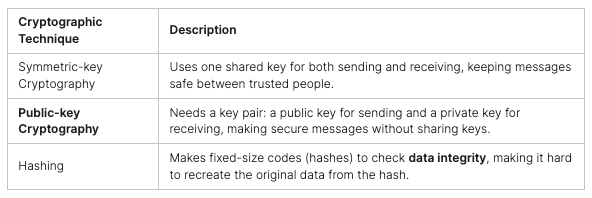
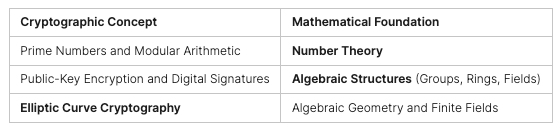
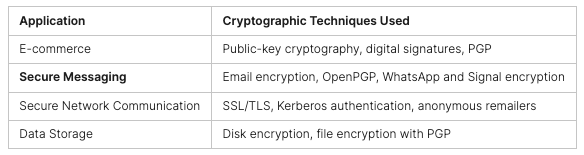
CTF challenges cover areas like Web, Forensics, Cryptography, Reversing, OSINT, and Miscellaneous. To do well, it’s key to have a good toolkit and keep up with cybersecurity trends.
Practicing is key in CTF competitions, with many contests offering past flags and solutions for practice. It’s also vital to take care of yourself during these intense events.
Networking is good, but be careful with team info and don’t share solutions online. Always read the rules of each CTF you join.
CTF competitions are a fun way to improve your hacking skills and can be very rewarding. TryHackMe and Hack The Box are great places to learn and prepare. TheHackersMeetup also hosts CTFs with prizes and limited spots.
*What is CTF? An introduction to security Capture The Flag competitions: https://youtube.com/watch?v=8ev9ZX9J45A
For those into the cybersecurity world, events like HackersHour are great for meeting other CTF fans and keeping up with new trends.
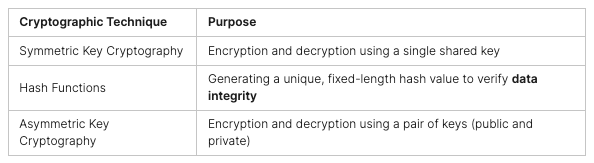
“Capture The Flag (CTF) competitions cover a variety of skills such as cryptography, steganography, open source intelligence, digital forensics, protocol analysis, penetration testing, vulnerability testing, threat hunting, website exploitation, and programming.”
CTF events can be Red versus Blue, Jeopardy-style, or individual/team games, with different time limits. Tools like Kali Linux and Oracle Virtual Box are often used.
Many platforms exist for practicing and honing your cybersecurity skills, such as PicoCTF and Cyber Skyline. Hacker101 CTF, TryHackMe, and GoogleCTF are also great options.
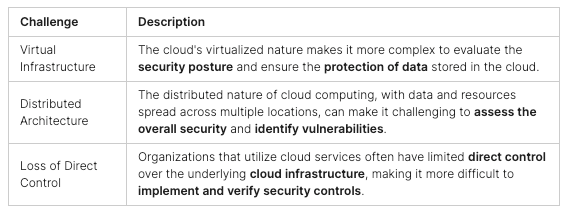
The Benefits of Participating in CTF Competitions
CTF competitions are key for boosting cybersecurity skills and cybersecurity education. They let participants get real-world experience in ethical hacking and problem-solving. Plus, they keep up with the newest cybersecurity trends and technologies.
Hands-on Cybersecurity Experience
CTF competitions give you a chance to use cybersecurity skills in real situations. You’ll face challenges like network analysis and finding vulnerabilities. By solving these, you’ll get a deeper understanding of cybersecurity concepts and improve your problem-solving.
Staying Updated with Trends and Technologies
These competitions focus on new cybersecurity threats like malware and phishing attacks. Taking part helps you stay current with cybersecurity trends and technologies. This is crucial for those looking to work in cybersecurity. It’s a great way to learn about the latest cybersecurity skills and methods.
“Employers value CTF experiences when hiring cybersecurity students, as it demonstrates initiative and technical skills.”

By joining CTF competitions, students boost their cybersecurity skills and learn about the latest cybersecurity trends and technologies. This practical experience and knowledge make them stand out in the fast-changing world of cybersecurity.
Networking Opportunities in CTF Competitions
Capture the Flag (CTF) competitions are a key spot for cybersecurity fans. They offer a chance to meet others who share your interests. These events draw in a mix of professionals, researchers, and students, making a lively cybersecurity community. Joining CTFs lets you make professional connections and talk about important topics with others in the field.
Jeopardy-style CTFs are great for networking. Teams tackle challenges to earn points fast and right. Attack-and-defense CTFs, where teams defend and attack, encourage teamwork and sharing of insights. These events boost your skills and keep you updated on the latest in cybersecurity.
CyberTitan, a Canadian event for students, offers real-world learning and helps grow the next cybersecurity leaders. Joining such events lets you meet future pros and help shape the cybersecurity community.
*How to Prepare for a Capture the Flag Hacking Competition: https://youtube.com/watch?v=adse5Zxw_I4
Running CTFs can be tough, needing setup and tools for everyone. But, using cyber ranges makes it easier. These platforms, like Field Effect Cyber Range, make joining in simple, boosting networking chances.
“CTF events provide a platform for participants to stay informed about current trends and technologies in cybersecurity.”
In summary, CTF competitions are a great way to make professional connections and be part of the cybersecurity community. They help you improve your skills and grow your network. This can boost your career and help the cybersecurity field grow.
Career Advancement Through CTF Competitions
CTF competitions are key for those wanting to move up in cybersecurity. They mimic real cybersecurity challenges and are known worldwide. These events let participants show off their skills, meet others in the field, and sometimes even get job offers.
CTF challenges cover many cybersecurity areas, like hacking, coding, and more. You can compete alone or with a team, depending on what you like. Working together helps improve teamwork and sharing knowledge.
Winning at CTFs has helped many cybersecurity pros, like Luis De la Rosa and others, grow in their careers. They say hard work, passion, and learning are key to doing well.
There are many CTF events worldwide, both online and in person. Events like PicoCTF and DEF CON offer great challenges and chances to meet others. DEF CON CTF is especially known for its tough challenges and top teams.
For those wanting to improve in offensive security, “Breaking & Entering” by Bishop Fox is a great guide.
In summary, CTF competitions are a big help for moving up in cybersecurity. They help you get better at your job, make important connections, and can lead to new job chances.
What Capture the Flag Competitions Teach Us About Cybersecurity
Joining Capture the Flag (CTF) competitions teaches us a lot about cybersecurity. It helps us get better at protecting our systems and data. These events let us see how hackers think and work, which helps us defend against them.
Teams work together in CTF competitions to solve challenges. This shows how crucial teamwork is in cybersecurity. Many experts say CTF is a top way to learn and use your skills safely.
CTF events are also great for meeting other cybersecurity pros. You can find mentors, potential jobs, and people who share your interests. This helps build a strong community and helps your career grow.
Cybersecurity Lessons from CTF Competitions:
- Understanding hacking techniques and mindsets to improve cyber defense strategies
- Emphasizing the importance of teamwork and collaboration in cybersecurity
- Providing hands-on experience to develop technical skills and expertise
- Facilitating networking and community-building among cybersecurity professionals
Using what we learn from CTF competitions, companies can get better at cybersecurity. They can stay ahead of threats and build a skilled cybersecurity team.
“CTF competitions are an invaluable tool for cybersecurity professionals to hone their skills and gain invaluable insights into the tactics and methods used by hackers. By understanding the mindset of the adversary, we can develop more effective cyber defense strategies and better protect our organizations.”
Organizations and Individuals Running CTFs
CTF competitions are now a key way for CTF organizers to test security safely. They draw in cybersecurity education and hacker training fans. They also attract those wanting to improve their ethical hacking skills.
CTFs for Cybersecurity Education
CTFs are becoming a go-to for teaching cybersecurity to students. They make learning about cybersecurity fun and spark interest in a career in info security. CyberTitan, a Canadian cybersecurity education event, is one example. It gives middle and high school students real-world learning experiences.
Big-name CTF events like Insomni’hack, 0CTF/TCTF, GoogleCTF, PlaidCTF, DEF CON, FAUST CTF, ASIS CTF Quals, Pwn2Win CTF, InCTF International, and RCTF offer big cash prizes and other rewards.
*Competitive Cybersecurity: Capture the Flag Contest: https://youtube.com/watch?v=R3YGrT3eOLo
These events offer great hacker training and ethical hacking chances. They also help CTF organizers check and grow cybersecurity skills.
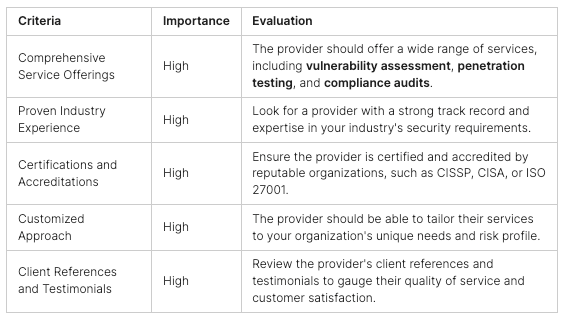
Challenges of Organizing CTF Competitions
Organizing a Capture the Flag (CTF) competition is tough. One big challenge is setting up a strong cybersecurity training space. This is often called a “cyber range.” It’s needed for the competition.
Using Cyber Ranges for CTF Competitions
Cyber ranges are like simulation labs for security training. They help organizers set up everything needed for CTF challenges quickly. These platforms have all the tools and resources teams need, making the competition easier to run. They also have features like scoreboards and timers that show team scores and activity in real-time.
Another big challenge is making the competition both fun and educational. It’s important to have challenges that test different cybersecurity skills. This includes things like digital forensics and web security.
Even with these challenges, CTF competitions are key for training in cybersecurity and finding new talent. By using cyber range platforms and designing good challenges, organizers can give participants a great experience. This helps grow the next generation of cybersecurity experts.
*Capture the Flag (CTF) 101: https://youtube.com/watch?v=wL3acu8xspM
“CTF events have been a staple at the DEFCON security conferences since 1996.”
Gamification of Cybersecurity Through CTFs
CTF competitions are a fun way to learn about cybersecurity. They started in the 1990s at hacker conferences, like DEFCON in Las Vegas, the biggest cybersecurity event in the U.S.. Now, teams from all over the world compete online for prizes and fame.
CTFs help people get hands-on cybersecurity experience. They boost skills, encourage critical thinking, and show dedication to employers. They also teach teamwork. Gamification, a growing field, makes cybersecurity training fun through CTFs.
There are different types of CTFs, like Attack-Defense and Jeopardy. Jeopardy challenges test many skills and reward quick solutions and difficulty. Most CTFs are for teams, usually no more than four, to improve teamwork.
Mastering CTFs can boost your career in cybersecurity and gamification. With 3.5 million cybersecurity jobs lacking worldwide, CTFs are a great way to fill this gap. They help keep IT and security pros sharp and attract new talent.
*I Played Beginner-Level Security CTFs For 30 Days – Here’s What I Learned: https://youtube.com/watch?v=Zw25_ySOrC0
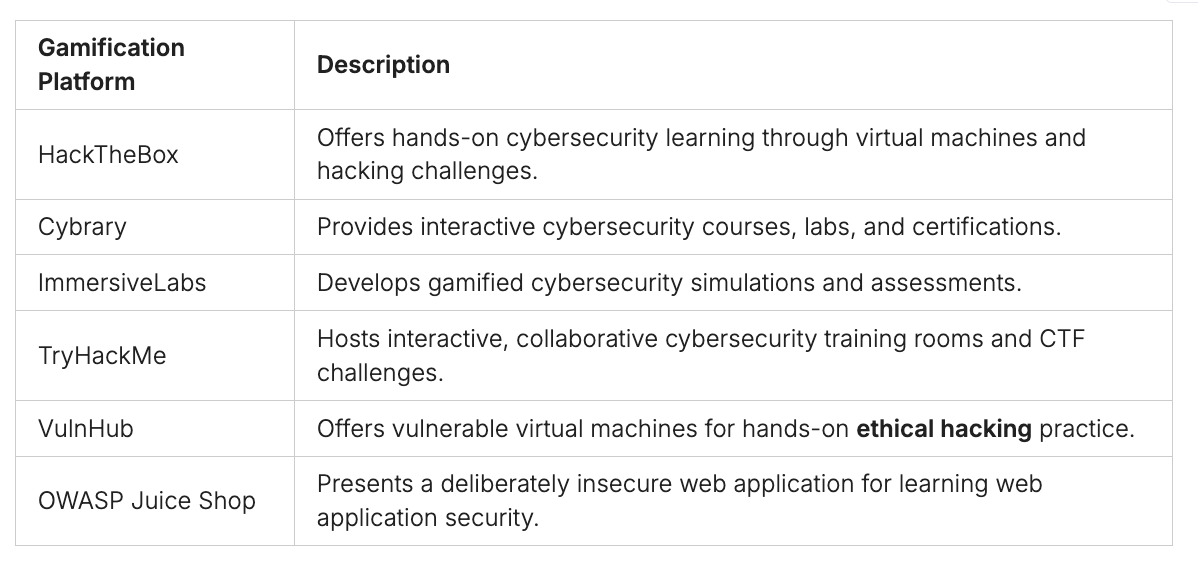
These platforms, along with CTFs and simulations, make cybersecurity training fun. Hackathons and gamified platforms teach cybersecurity skills in engaging ways. eSports platforms let people watch and learn from ethical hacking competitions.
“Attitude is considered the most critical factor for entry into CTF competitions rather than specific skills.”
In conclusion, CTF competitions make cybersecurity learning exciting for students and professionals. They improve critical thinking, teamwork, and passion for the field. This helps fill the cybersecurity skills gap and opens up new career paths in this fast-changing industry.
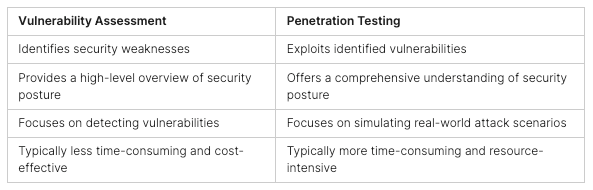
CTF Content and Challenge Types
CTF competitions are a big deal for cybersecurity fans. They test skills and keep folks updated on the latest in security. These events have many challenge types, each testing different cybersecurity skills.
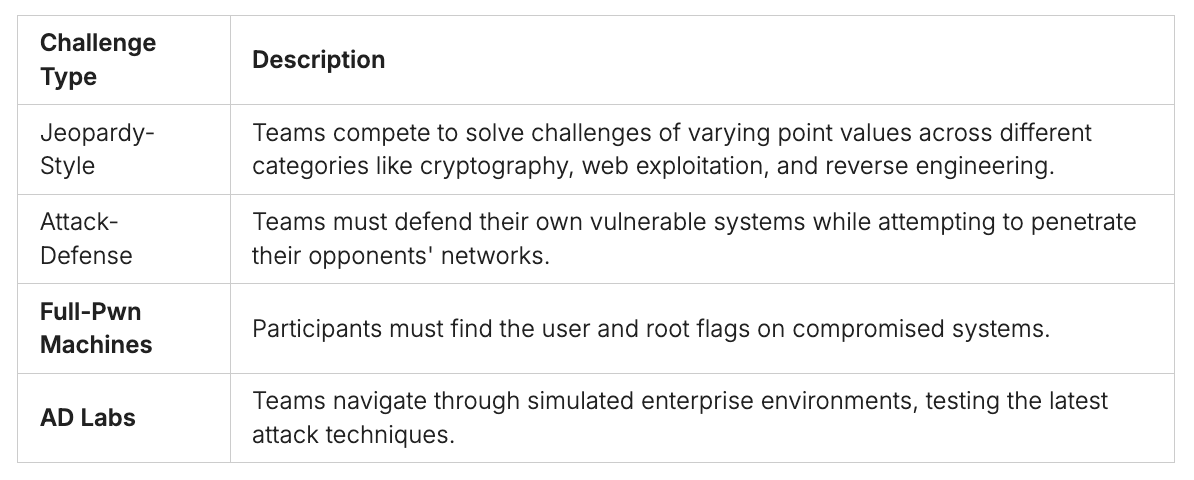
Jeopardy-Style Challenges
Jeopardy-style CTFs are quite common. Teams face many challenges or questions, each worth points. They cover topics like cryptography, web exploitation, and reverse engineering.
Full-Pwn Machines and AD Labs
CTFs also feature full-pwn machines and AD labs. In full-pwn machines, teams aim to find flags on compromised systems. AD labs mimic real-world settings, testing new attack methods.
CTF challenges are key in cybersecurity training and learning. They offer hands-on experience in a fun way. With various challenges, CTFs improve skills in vulnerability analysis, exploit development, and incident response.
CTFs in Academia and Corporate Training
Capture the Flag (CTF) competitions are now popular in schools and companies. They make learning about cybersecurity more hands-on and fun. Students get to solve real-world problems, improving their skills. Companies use CTFs to boost employee skills and make training fun with a game-like approach.
The European Union Agency for Cybersecurity says the top CTF types are Jeopardy and Attack-Defense. These events test many skills, like hacking, defending, and analyzing network traffic. Winners can get cash, recognition, scholarships, or spots in more challenging CTFs, encouraging more people to join.
However, CTFs might be tough for those new to cybersecurity. They often focus on quick attacks, not the slow, real-world kind. This can make the challenges less like real situations.
To fix this, schools and companies can use cyber ranges for more realistic CTFs. Adding game elements and practical training helps bridge the gap between theory and practice. This makes participants better prepared for real cybersecurity challenges.
Using CTFs in training shows their value in building a skilled cybersecurity workforce. As cybersecurity needs grow, CTFs will likely play a bigger role in training.
Conclusion
Capture the Flag (CTF) competitions are essential for enhancing cybersecurity skills for both professionals and students. These events provide practical experience in cryptography, reverse engineering, web exploitation, and forensics, simulating real-world cybersecurity challenges to test your skills and problem-solving abilities.
Participating in CTFs not only hones your abilities but also connects you with peers in the field. Many cybersecurity experts attribute their growth to these competitions. With durations ranging from a few hours to several weeks, CTFs offer an engaging and competitive learning environment, featuring live leaderboards that make the experience enjoyable and motivating.
As cybersecurity becomes increasingly critical, CTFs are recognized as valuable tools in educational institutions and organizations. They facilitate skill development, knowledge sharing, and exposure to the latest cybersecurity trends. By incorporating CTFs, schools and businesses can effectively train the next generation of cybersecurity leaders, preparing them to face future digital threats.
Join our community at Peris.ai Cybersecurity to elevate your skills and connect with like-minded individuals. Visit Peris.ai to learn more about our events and how you can get involved. Secure your digital future with Peris.ai today!
FAQ
What are Capture the Flag (CTF) competitions?
Capture the Flag (CTF) competitions test your skills in finding and using system weaknesses to get a “flag” or info. They come in different styles. Some are like jeopardy games where teams race to solve challenges fast and right. Others are attack-and-defense games where teams defend their systems and try to break into others.
What are the benefits of participating in CTF competitions?
CTF competitions offer many perks. You get real cybersecurity experience and improve your skills. You also keep up with new trends and tech. Plus, it’s a chance to meet others in the field and could lead to a cybersecurity career.
How can CTF competitions inform cybersecurity best practices and defense strategies?
CTFs give insights into hackers’ ways and methods. This helps cybersecurity pros develop better defenses. By knowing how hackers work, you can create stronger security for your organization.
What types of CTF challenges are commonly used?
There are many CTF challenges. You might find jeopardy-style, attack-and-defense, full-pwn machines, or Active Directory labs. These simulate real-world scenarios to test your skills.
How are CTF competitions being used in academic and corporate settings?
CTFs are used in schools and companies to improve cybersecurity training. In schools, they make learning more practical by facing real-world challenges. For companies, they boost skills and awareness, making training fun and effective.