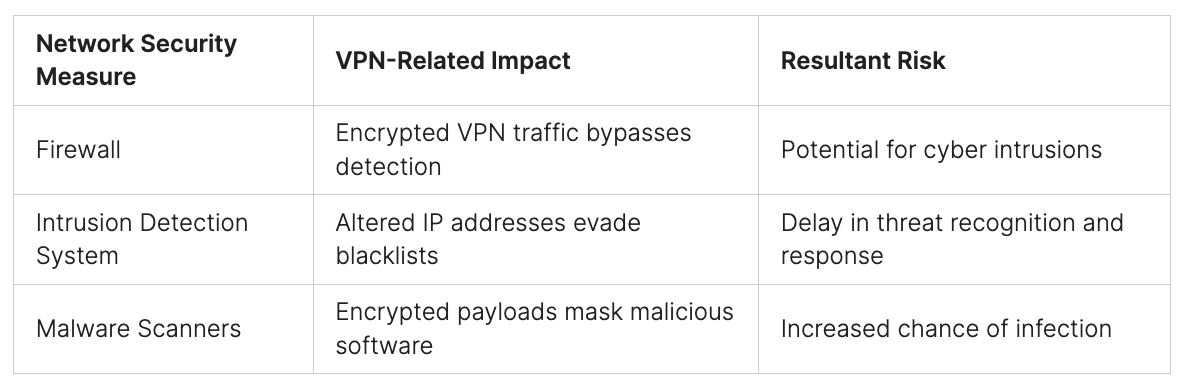
In the fast-changing world of cybersecurity, hackers are always finding new ways to break into our systems. This means businesses need the best tools to spot and stop threats. SOAR tools are one such powerful resource. They help us fight cybercrime by automating and coordinating security tasks. But what is SOAR exactly, and how does it change our security approach?
SOAR is about making security work more automatic and organized. This lets security teams handle their toughest jobs more easily. By bringing together data from different security tools, they can better deal with threats. Also, SOAR can do many small security tasks by itself. This speeds up responses, makes us smarter about threats, and helps security workers focus on bigger issues.
With many SOAR options available, picking the right one for your business can be tricky. This guide covers 10 top SOAR platforms. You will learn what each one offers and how it fits different security needs.
So, what makes the best SOAR solutions stand out? And how do they change the security game? Let’s explore and find out!
Key Takeaways
- SOAR solutions bring together security jobs to work more smoothly.
- They make responses quicker, help us understand threats better, and ease the load on security staff.
- This guide will look into 10 key SOAR platforms and what makes them special.
- Today’s businesses need advanced security to tackle the rising number of online threats.
- SOAR’s knack for automating and organizing security tasks is reshaping security strategies.
Cybersecurity Threats and the Need for SOAR
The number of cybersecurity threats keeps rising, so more businesses are going online. Yet hackers are finding new ways to break through security. Companies must now use advanced, sophisticated detection and response methods to stay safe from cyber-attacks.
Increasing Cyber Attacks and Online Operations
The more cybersecurity threats we see, the more vital good security becomes for businesses. With online work growing, protecting digital activities is key, making strong security solutions very important.
The Importance of Sophisticated Detection and Response Methods
The old security ways are not enough to face today’s threats. Businesses need sophisticated detection and response methods that actively stop threats. This is why SOAR tools are becoming essential for improving cybersecurity.
What is SOAR?
SOAR stands for Security Orchestration, Automation, and Response. It combines three important security tools: security orchestration, security automation, and incident response.
Security Orchestration
It links different security tools inside and outside a company. This is done by using built-in connectors or creating new ones. These tools can include scanners, antivirus software, and monitoring systems.
It also includes user behavior checks and information from security alerts. Doing this helps spot dangers faster and respond better.
Automation
Automation in security means using machines to do tasks instead of people. It uses data and warnings from the security system to handle important but routine jobs without needing a human to do them each time.
For example, it can look for weak points in the digital armor, check logs for unusual activity, and keep track of tasks. These are things that would keep a human worker busy. It’s like having an extra expert on hand.
Incident Response

After a threat is found, there’s much work to protect against it. Incident response is the part of SOAR that helps here. It keeps everyone working on security informed and focused.
This means teams that handle security might share information and work together to fix the problem. It also tracks what happens after the threat is over to learn and improve. Think of it as a way to get better every time something goes wrong.
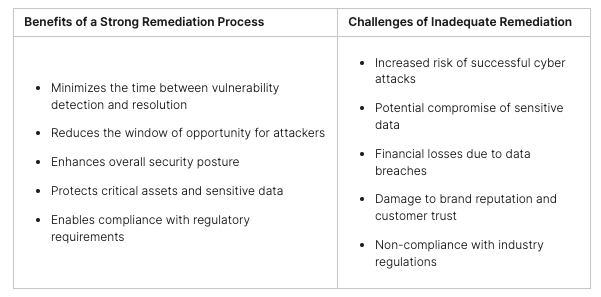
The Benefits of SOAR
Using a SOAR solution has many benefits for companies. It allows them to react faster and spend less money. With SOAR’s help, teams can handle data and issues quicker and more efficiently.
Faster Response Times
SOAR makes it simpler to spot and tackle security issues, softening hackers’ effects. This is all thanks to how SOAR merges data and actions smoothly.
Increased Threat Intelligence
SOAR gathers data from many tools and gives a better picture of threats. Teams can thus decide and act more wisely. They know more about current threats.
Reduced Manual Operations
SOAR takes care of the small security problems by itself. This way, human teams can focus on the bigger issues. They react faster to the things that really need hands-on work.
Streamlined Security Operations
By using the same plans for common tasks, teams handle more in less time. Everybody follows the same fix-it steps. This keeps security settings in top shape across the whole company.
Lower Costs
SOAR means fewer need to do security tasks by hand. This saves much money. It’s better than having people do everything on their own.
Key Features to Look for in a SOAR Solution
When you’re looking at SOAR solutions, make sure they have certain important features. Check for dynamic case management, an API-first setup, and easy integration. Also, look for solutions that promise high availability and disaster recovery.
Dynamic Case Management System
SOAR tools collect information from many places and put it all together for quick analysis. This helps analysts solve problems faster by giving them the full picture in one place. They sort through the necessary info without distraction.
API-first Architecture
Taking an API-first approach means the SOAR tool can easily grow with your company. It connects new software or hardware easily because it’s built to adapt. This setup means your security system stays strong even as your business changes.
Simple Integration Framework
Choosing a SOAR solution that’s easy to integrate with your existing tools is key. It should also let you customize and create new scripts so you can add new tech without a headache.
High Availability and Disaster Recovery
Your SOAR tool has to be dependable. If it fails, it could stop your security operations. So, make sure whatever SOAR solution you pick can keep your business running even when there are problems.

The Ultimate SOAR Guide
In today’s world, security orchestration, automation, and response (SOAR) tools are key in fighting threats. They merge data from various security tools, handle repeating tasks, and make responding to incidents smoother. This boosts organizations’ overall security.
The Ultimate SOAR Guide outlines the main features and perks of this new tech and equips security teams with the knowledge they need to navigate the ever-changing SOAR world. With SOAR, companies can respond quicker, spot threats more accurately, perform fewer tasks manually, and save money on their security work.
With cybersecurity always changing, the call for smart security automation and incident response options is loud. The Ultimate SOAR Guide gives security experts tips to work in this fast field. It helps them use top security orchestration plans to keep their organizations safe from more cybersecurity threats.
10 Solutions That Are Transforming Security Operations!
The following SOAR solutions on the market can assist in achieving the desired efficiency:
1. Chronicle SOAR
Chronicle SOAR is part of the Google Cloud umbrella, designed to enable companies to collect information and alerts about security through automation, orchestration of threat intelligence, and incident response. It is integrated with Chronicle SIEM to ensure both applications can work efficiently based on the most current information.
Features
- Effective case management that can process, classify, prioritize, assign and then investigate alerts
- Playbook creation based on zero-code
- Effective investigation capabilities that focus on the root of threats and not alerts.
- The threat intelligence system is integrated throughout the lifecycle of detection and response.
- Collaboration is easy – you can increase efficiency through incidental collaboration and openness.
- Raw log scans are a way to scan unprocessed data for new insights.
2. FortiSOAR from Fortinet
Fortinet is a leading California-based cybersecurity firm with a wide range of firewalls, intrusion prevention and endpoint solutions available. Fortinet FortiSOAR is the company’s SOAR solution. It gathers information from various sources and combines it into manageable, actionable intelligence.
Features
- More than 350 integrations and 3,000 automated workflow actions
- 160 playbooks with customizable playbooks out of the box
- Innovative threat intelligence and management due to its integration into FortiGuard
- Mobile applications that allow analysts to take action on alerts and perform critical actions
3. Palo Alto Networks
With its headquarters in California, Palo Alto Networks is a world leader in enterprise security. Cortex XSOAR comes with Cortex threat protection, intelligence management, Palo Alto Networks, and response capabilities. All of these elements create Cortex XSOAR, a powerful and sophisticated choice.
Features
- More than 750 integrations and 680 plus content packs
- The ability to operate entirely automated or with SOC supervision
- Corresponds to data points within a designated “war room”, which allows human-based investigation
- Incorporate data from all the major SIEM tools
- The threat intelligence management (TIM) module provides the context of the alerts
- Integrations can be customized and downloaded via the Cortex XSOAR marketplace.
4. ThreatConnect SOAR
Established in 2011, ThreatConnect is a cybersecurity company that is an expert in threat intelligence and analytics and quantifying cyber risks. The SOAR platform integrates seamlessly with various security tools to coordinate investigations, provide information, and offer more effective responses.
Features
- Automated tasks with an editor that can be dragged and dropped.
- Utilize historical data to help sort out alerts so that you can focus on important tasks.
- A vast array of threat-hunting capabilities utilizing workflow templates and automated processes
- Analysis of Malware and Phishing attacks and response
- A myriad of built-in playbooks
- Blocking and detection of threats using high-fidelity intelligence
5. Swimlane SOAR
Swimlane is a leading Colorado-based SOAR provider that specializes in security-related automation. The platform can collect alerts and data from various sources and automate the response to incidents and operational workflows. It is low-code, making remediation playbooks much easier to develop and visualize. The platform can be used either on-premises or via cloud services and is priced per user. This makes the solution flexible and easy to deploy.
Features
- Coordinate workflows and manage workflows using easy-to-configure playbooks.
- Powerful case management
- Advanced reporting dashboards
- Open and customizable platform—This allows SOC teams to develop the tools they require to address various challenges and use cases.
6. Splunk
Splunk is a leading software company that specializes in helping businesses find, monitor, and analyze data using its robust data platform. Splunk SOAR is a highly effective solution that facilitates collaboration and participation through security automation and response workflows.
Features
- Integration with over 350 different tools
- Includes 100 playbooks that are included in the box.
- Visual editor to edit code-free
- Threat intelligence enhanced through Splunk SURGe security research group.
- Highly effective case management tools
- Mobile app Linked SOAR lets SOC teams deal with threats or triage alerts, write playbooks, and collaborate anytime and from anywhere.
7. Sumo Logic
Sumo Logic is based in California and provides data analytics for operations, security, and business. Cloud SOAR is a full-featured solution that allows SOC analysts to reduce alert noise, streamline incident triage and responses, and improve collaboration. The solution is available as SaaS, on-premises, or cloud-based, which makes it simple to integrate it wherever you want to work.
Features
- Complete automation of the lifecycle of an incident
- Advanced threat triage using ML eliminates false positives or duplicate incidents.
- IOC investigation, as well as incident classification and alert enrichment
- Built-in playbooks with an effective design that makes use of data from the past to determine the most effective treatment
- Custom-designed reports and dashboards that can be customized to monitor IOCs and workflow processes, and performance indicators
8. ServiceNow Security Incident Response (SIR)
ServiceNow, founded in 2014, is an IT, digital workflow, and business management leader. Security Incident Response (SIR) is an effective SOAR-based cloud solution that’s a component of the Security Operations (SecOps) Platform.
It permits SOC teams to handle and react to emergencies, facilitate collaboration, and speed up processes. The SecOps platform also includes vulnerability management, incident response, threat intelligence, and tools to ensure configuration compliance.
Features
- Automate workflow and coordinate response
- An extensive library of playbooks and orchestrations for a variety of scenarios
- Additional applications are available through the ServiceNow store.
- Artificial Intelligence tools for incident investigation
- Virtual war room to facilitate collaboration
- Real-time, real-time reporting capabilities
9. Rapid7 InsightConnect
Rapid7 is a cybersecurity company based in Boston. It uses enhanced visibility, analytics, and automation to protect digital environments. InsightsConnect is Rapid7’s SOAR platform, which was gained from Komand’s platform and acquired in 2017. This resulted in a robust cloud-based SOAR system that simplifies workflows and processes and allows you to concentrate on other urgent issues.
Features
- Automate workflows with no code
- Over 200 plugins and flexible workflows
- ChatOps lets you integrate with other apps, such as Slack or Microsoft Teams.
- Automated third-party products using InsightConnect Pro Automation
- Automated investigation and response to threats such as phishing and ransomware
- Management of vulnerability through human decision-making and cross-functional collaboration
10. Devo SOAR
Devo (formerly part of LogicHub) is a cybersecurity company founded in the year 2011 and is focused on intelligence-driven threat detection and response solutions. Devo SOAR is one of the best SOAR solutions available in the market. It provides end-to-end automation and helps security teams improve collaboration and efficiency. It can efficiently prioritize and triage alerts so that you’re able to filter out the noise and concentrate on the most crucial problems.
Features
- All phases of the threat lifecycle could be automated.
- Over 300 standard integrations that make it easy and quick integration
- Playbooks are pre-built and customized, edited and modified without programming.
- Effective triaging and the ability to block out noisy alerts
- Simple case management tools that can be adapted to your workflow
Conclusion
In today’s dynamic cybersecurity landscape, SOAR solutions have become indispensable. They allow companies to integrate data from multiple sources, automate security tasks, and expedite incident response. Among these solutions, Brahma Fusion from Peris.ai Cybersecurity stands out as a cutting-edge unified connector that revolutionizes security operations through seamless automation and orchestration.
Why Choose Brahma Fusion?
- Unified Connector: Integrates various security tools and platforms, enhancing efficiency and reducing manual intervention.
- Customizable Security Response: Tailor’s security protocols to specific threats and operational requirements, ensuring precise and effective responses.
- Drag-and-Drop Complex Workflow: Simplifies the creation and management of complex security workflows with an intuitive interface.
- Custom Code for Precision: Allows for the incorporation of custom code into security workflows, addressing unique security challenges with unparalleled precision and control.
Benefits of Brahma Fusion:
- Enhanced Efficiency: Streamlines cybersecurity workflows, reducing manual errors and saving time.
- Operational Agility: Provides scalability and flexibility, adapting to the unique needs of different environments and evolving threats.
- Improved Security Posture: This ensures timely and coordinated task execution, resulting in a more secure and responsive infrastructure.
- Significant Time and Cost Savings: Reduces the workload of security teams, allowing them to focus on critical issues and improving overall productivity.
Brahma Fusion Features:
- Customizable Security Response: Tailor your security protocols to specific threats and operational requirements for precise and effective responses.
- Drag-and-Drop Complex Workflow: Easily create, modify, and deploy intricate security workflows with an intuitive interface.
- Custom Code for Precision: Incorporate custom scripts and logic into your security workflows for optimal performance and adaptability.
- User-Friendly Interface: Simplifies the management of complex security operations with a powerful orchestration engine.
As threats continue to evolve, investing in advanced SOAR solutions like Brahma Fusion is a smart move for any security team. By leveraging its innovative features, organizations can enhance their defense capabilities, streamline operations, and ensure the protection of their critical systems and information.
Discover how Brahma Fusion can transform your cybersecurity operations. Visit Peris.ai Cybersecurity to learn more about our advanced solutions and how we can help you stay ahead of emerging cyber threats. Secure your organization’s future with Brahma Fusion today.
FAQ
What is SOAR (Security Orchestration, Automation, and Response)?
SOAR is a smart way to tackle security issues. It combines three big ideas: security control, doing things automatically, and reacting quickly. It links different security tools together, does some security jobs by itself, and makes reacting to problems smoother.
How does SOAR improve security operations?
SOAR makes finding and dealing with dangers faster. It does this through using automated plans. It adds more details, does deeper checks, and brings in the latest threat info. This helps people make smarter, faster choices when a problem shows up.
What are the key benefits of SOAR solutions?
The main benefits of using SOAR are that it allows for faster action, knowledge of threats, less manual work, smoother security work, and lower costs.
What features should I look for in a SOAR solution?
If you’re considering SOAR options, focus on a system that allows you to manage cases flexibly, an architecture that starts with APIs, easy teaming up with other tools, and being ready to keep working even if things go wrong.
Which SOAR solutions are available in the market?
There are top SOAR solutions like Chronicle SOAR, FortiSOAR from Fortinet, Palo Alto Networks, ThreatConnect SOAR, Swimlane SOAR, Splunk, Sumo Logic, ServiceNow Security Incident Response (SIR), Rapid7 InsightConnect, Devo SOAR and Brahma Fusion from Peris.ai Cybersecurity.